Creating IAM Policy and Role
Creating IAM Policy and Role
As last of this part, we are creating IAM Policy and Role for Full Stack Application.
-
Firstly, making Policy for Role. In this lab, we are using AWS Managed Policy for comfort. Move to IAM menu on console. https://console.aws.amazon.com/iam
-
Select Policies on menu, and click Create Policy button.
-
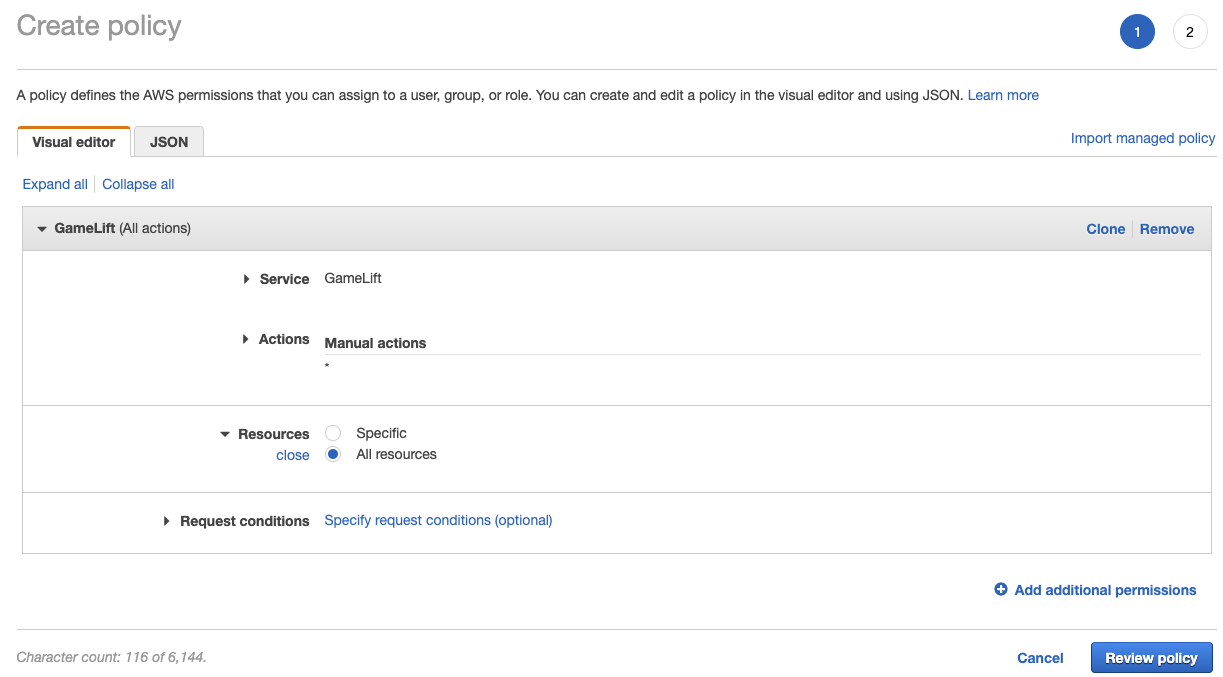
Select GameLift on Visual Editor > Service. For Actions, we are selecting “All GameLift actions” for comfort. Click “Review Policy”.
-
Put Policy Name(GameLiftFullAccess) and Click “Create policy” Button.
-
Nexly, we are creating five IAM Roles for Lambda functions.
-
Move IAM Console > Role menu, and click “Create Role” button.
-
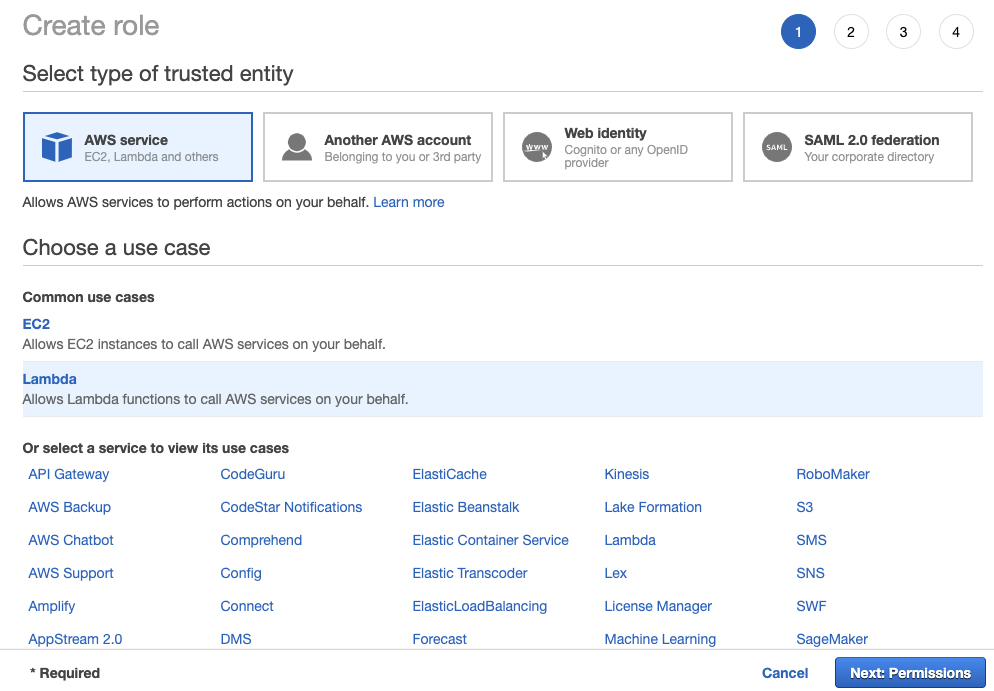
Select AWS Lambda for Role Type.
-
Allocate 3 IAM policies on this Role. Select Policies (AmazonSQSFullAccess, AmazonDynamoDBFullAccess, AWSLambdaBasicExecutionRole) on the editor.
-
Put Tag as an option, and Click Next:Review. Role Name would be “Gomok-game-sqs-process”.
-
Click “Create role” button to create first IAM Role.
-
Creating second role is also similar. For this role, choose AmazonDynamoDBFullAcess, AmazonVPCFullAccess, AWSLambdaBasicExecutionRole as Permission.
-
Designate Role name as “Gomok-game-rank-update”.
-
Third role is also similar. Let’s set AmazonVPCFullAccess, AWSLambdaBasicExecutionRole policies for this Role.
-
Set role’s name as “Gomok-game-rank-reader”.
-
Creating fourth role uses Policy that we made above(GameLiftFullAccess). Let’s put permissions AWSLambdaBasicExecutionRole, AmazonDynamoDBFullAccess, and GameLiftFullAccess for this Role.
-
Set its name as “Gomok-game-match-request”.
-
Last Role will also be same. It should contain AWSLambdaBasicExecutionRole, GameLiftFullAccess Policies as permissions.
-
Name of last role would be “Gomok-game-match-status”
-
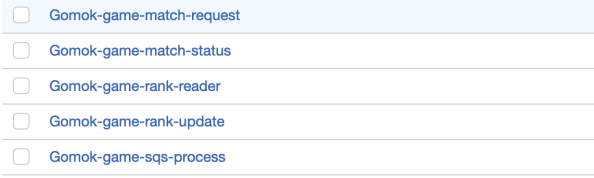
Creating all IAM Roles, you can find roles below!
-
Lastly, make additional Role for GameLift. Roles that we made before were used for Lambda functions, but this role is for GameLift Fleet. GameLift Fleet needs to access SQS for Game Result Processing.
-
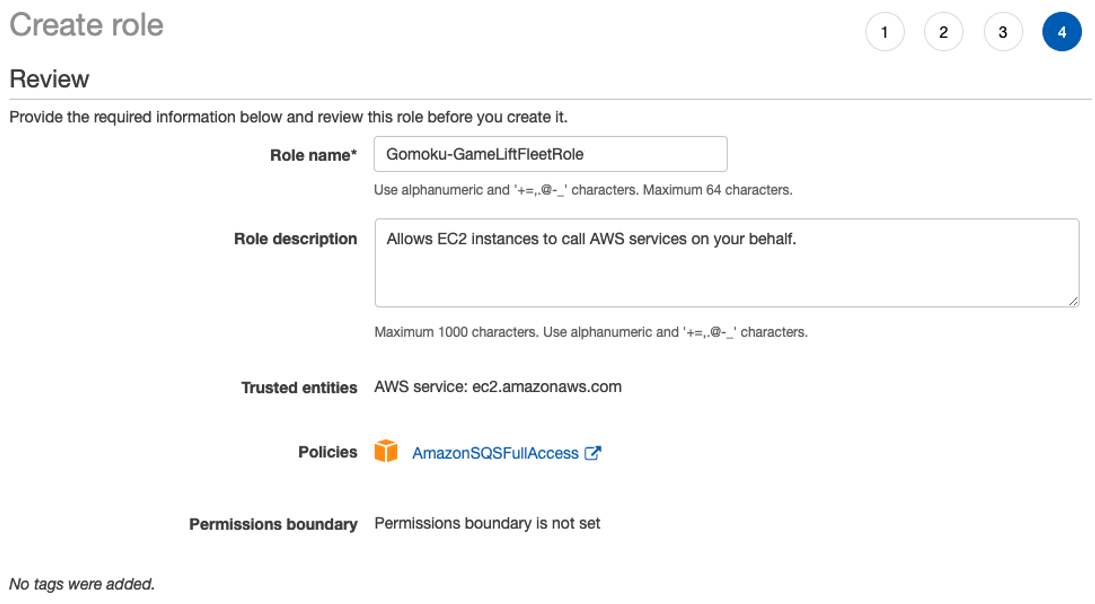
Click “Create Role” and make new Role. We should select “GameLift” as Service, but for now select “EC2” as service, and move next.
-
Select AmazonSQSFullAccess as Permission, and set role name as “Gomoku-GameLiftFleetRole”.
-
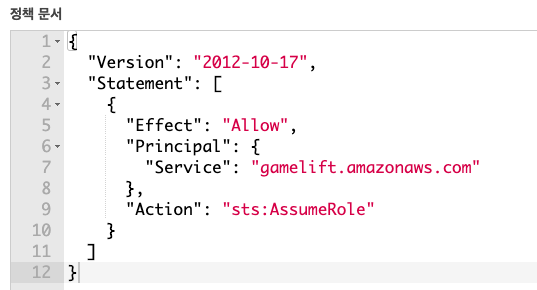
We should change service that uses this Role to GameLift. Select “Gomoku-GameLiftFleetRole” on console, and select “Trust relationships” tab. Click “Edit trust relationship” button.
-
Change settings like below. It will be changed “ec2 -> gamelift”. Save with “Update Trust Policy” button.
This is all about first part on this lab. :) No so complicated. right?
Let’s make Game server on next part.